Coronavirus-themed domain registrations are 50% more likely to be from malicious actors, Check Point Software Technologies Ltd. CHKP, -2.92% found in a study. Since that report was released last week, there have been some high-profile examples, most notably an attack aimed at a popular interactive COVID-19 tracking map maintained by Johns Hopkins University.
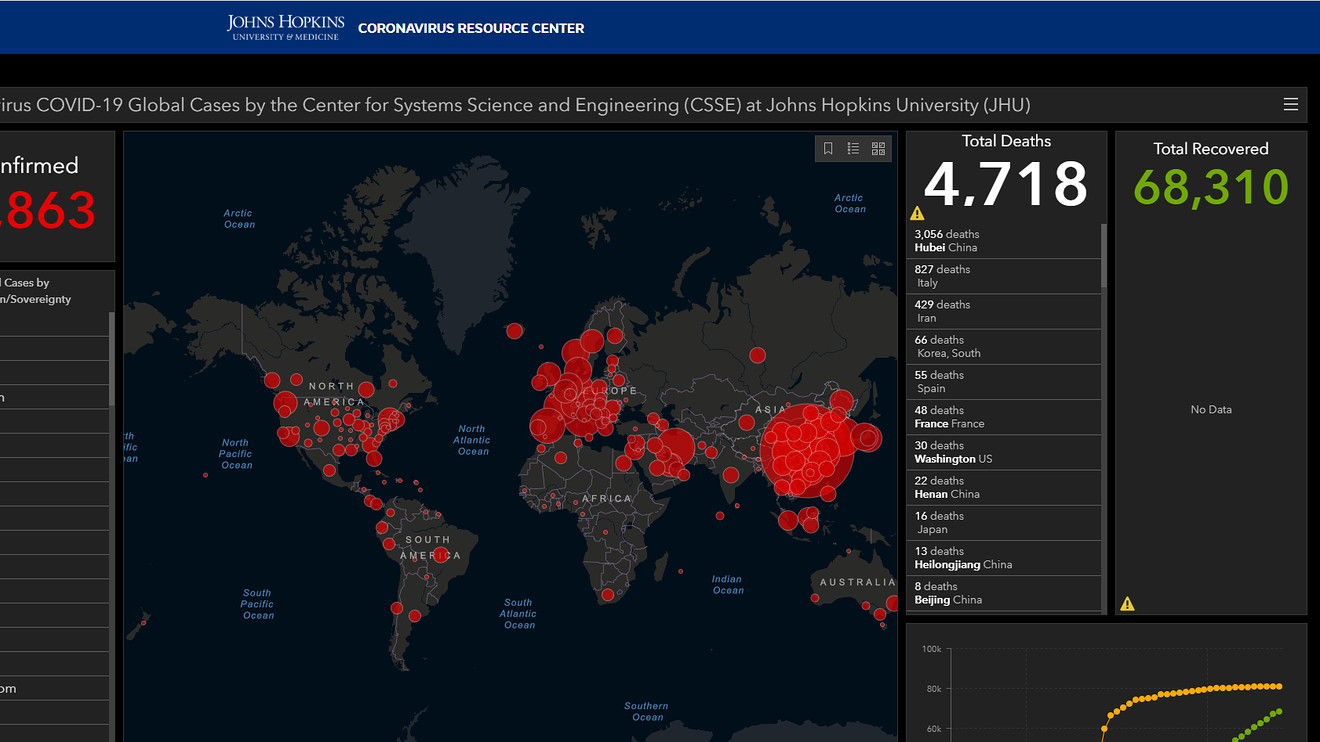
Noted security blogger Brian Krebs reported Thursday that the map has been targeted by hackers who are selling malware claiming to compromise the map and infect users. Johns Hopkins spokeswoman Jill Rosen said the university is aware of the malware that impersonates its COVID-19 site, and warned users to only trust the maps at its own site and one maintained by ArcGIS. The malware requires users to download software to generate the fake map, Rosen told MarketWatch.
“If you receive an email containing a link to download such an item or come across the code for the malicious app please report it immediately to the Esri incident response team through ArcGIS Trust Center security concern page,” Rosen said in a statement.
Just as doctors say frequent hand-washing and respiratory hygiene is the best defense against the coronavirus, cybersecurity professionals stress that computer users need to be more wary of what they click, such as not downloading an email attachment from an unknown source, and other tips offered by the Cybersecurity and Infrastructure Security Agency.
Read: Working from home because of coronavirus? Don’t give your company a different kind of virus
These ploys of tricking computer users to download malware by tapping into fear and anxiety are as old as the internet, said Charles Poff, a chief information security officer at SailPoint Technologies Holdings Inc. SAIL, -20.99%
“Despite international efforts to quell the virus, the World Health Organization recently classified this as a global pandemic; online scammers are trying to exploit this uncertainty through phishing attempts and bunk domain names,” Poff said.
“An email seemingly from the CDC is trying to lure vulnerable people into clicking links to learn more about the virus but ultimately leading them astray,” Poff said. “Not only am I recommending people to be cautious about opening email and files received from unknown senders, but also to beware of look-alike domains that are phony websites.”
SailPoint noted that students and staff from universities that were canceling classes were also falling prey to hackers. Discovered by San Francisco-based Abnormal Security, one attack uses an email that looks like it is coming from the school’s “health team” leading to a fake login page that tries to steal the victim’s credentials.
Similarly, Proofpoint Inc. PFPT, +3.64% has found attacks using emails promising coronavirus cures or spoofing the World Health Organization.
Check Point researchers said Thursday that they found hackers based in China have been using rich text format, or RTF, coronavirus warnings against public-sector workers in Mongolia. If a target opens the RTF document, it attacks Microsoft Corp.’s MSFT, -14.73% Word application, and seeks to take screenshots, list files, and directories and download files.
“In this campaign, we observed the latest iteration of what seems to be a long-running Chinese- based operation against a variety of governments and organizations worldwide,” Check Point researchers wrote. “This specific campaign was leveraging the COVID-19 pandemic to lure victims to trigger the infection chain.”
“The full intention of this Chinese [advanced persistent threat] group is still a mystery, but they are here to stay; updating their tools and it seems they will do whatever it takes to attract victims to their network,” the researchers wrote.
“We have observed espionage actors from China, North Korea, and Russia exploit this topic in spear-phishing campaigns,” Ben Read, senior manager of intelligence analysis at FireEye Inc.
Source: MarketWatch




Post a Comment